Modern communication relies heavily on Wireless Networking and it is therefore gaining popularity for Home and Business Networking. Wireless Networking offers the advantage of mobility and eliminates the use of cables. Computers at home or in a small office can easily be connected through Wireless Networking.
Setting up a secured network through a Netgear or any Router will keep your data free from spying and avert entry of any uninvited user into your network. You will have to follow certain guidelines to set up a Secured Wireless Network that will be provided either through Wireless Protected Array (WPA) or Wireless Encryption Protocol (WEP).
GUIDELINES
Connect to Modem
Power off your modem.
Connect one end of the Ethernet Cable to the ‘input’, marked at the backside of the router and other end to the modem.
Power Modem back on.
Generally it is a good rule to wait at least a minute before continuing to the next step.
Connect to Computer
· Connect one end of a second Ethernet Cable to one of the available ports on the Router. Most modern Routers include four ports.
Power your Router
· Plug your Router to a power source and wait till until your Router’s LED signals that it is connected to the internet. Generally Routers have a green LED indicator that turns solid when connected.
Install Software and Drivers
· If your Router included a disk to install Drivers, insert disk and continue following the disks instructions to install Drivers and set up your Network.
· If your Router does not include a disk continue to next steps.
Configure your Network
· Take note of the Router’s IP address that is selected automatically (default) and mentioned in the user’s guide. Most Routers by default use, http://192.168.1.1 as the default IP address
· Open your default web browser and type in the router’s address in the provided empty search field.
· Insert a valid Username and Password. If you have not set one up and it requires one, the default for most brands of Routers is, Username: Admin, Password: Password.
· You can also get to your Routers (Homepage) by going to Start Menu\Control Panel\Network and Sharing Center. Click the center icon at top, which usually has the house as an icon if you saved your Network as a Home Network. On the next page under Network Infrastructure you should see your Router listed. Just Right-Click your Router Icon and you should have a menu option to view Homepage.
Basic settings
· Choose your Basic Settings such as Router Name, and IP Addressing
· Locate Wireless Security or Wireless Settings. Choose a name(SSID) for your Network that you can easily identify and whether you wish to broadcast your Wireless Signal.
· Select channel to broadcast on, by default a Router usually has this set to Auto which is fine for most users.
· Select Wireless Mode. This is your speed for your wireless. Example: 54Mbps, 145Mbps and 300Mbps.
For your Wireless Security settings, most modern Routers include the following types of security:
· None – No security. Not recommended if you are in an area where someone who lives next door to you could use your Wireless Connection to connect to the Internet.
· WEP – Older security encryption used for Wireless Networks with better options now available. This option does not give a password but a unique key that users enter to connect. · WPA-PSK[TKIP] – Better security than WEP and sometimes users still use this if they have issues with devices connecting. Still a great Security Option. There is a 54Mbps limit on this connection using Legacy G.
· WPA2-PSK[AES] – Newer security using N support and if you have no issues with devices connecting this is the recommended Security Option as it gives you the best security. · WPA-PSK[TKIP]+WPA2-PSK[AES] – If you have issues with devices connecting you can use this setting as it gives you a combination of WPA and WPA2.
Another thing to note outside of setting up your Router is setting up Sharing for Computers and Devices connected to your Network. Windows 7 has come along way in making this easier for users and most users can do this by following the walk-through in Windows.
Source : http://www.thewindowsclub.com
 Copy both these files to your PC and create a shortcut for Glink to the Desktop. Edit the Contacts.ini file (in notepad) as per your need. You can add up to 100 email IDs.The Sender name in the ini file must be your name. You can however change the name when using the exe.
Copy both these files to your PC and create a shortcut for Glink to the Desktop. Edit the Contacts.ini file (in notepad) as per your need. You can add up to 100 email IDs.The Sender name in the ini file must be your name. You can however change the name when using the exe.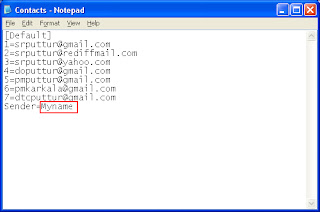 Contacts.ini file
Contacts.ini file Copy both these files to your PC and create a shortcut for Glink to the Desktop. Edit the Contacts.ini file (in notepad) as per your need. You can add up to 100 email IDs.The Sender name in the ini file must be your name. You can however change the name when using the exe.
Copy both these files to your PC and create a shortcut for Glink to the Desktop. Edit the Contacts.ini file (in notepad) as per your need. You can add up to 100 email IDs.The Sender name in the ini file must be your name. You can however change the name when using the exe. Contacts.ini file
Contacts.ini file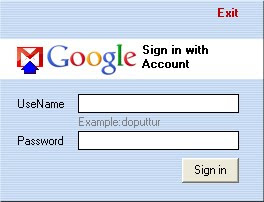 In the Login screen, type your gmail ID. Press Enter. Please note that the ID should not contain@gmail.com. Then type the Password of your google ID. Press Enter or click Sign in. If you do not want to continue, you can click exit which closes the application.
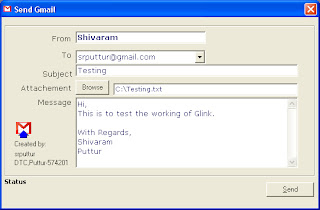
In the Login screen, type your gmail ID. Press Enter. Please note that the ID should not contain@gmail.com. Then type the Password of your google ID. Press Enter or click Sign in. If you do not want to continue, you can click exit which closes the application.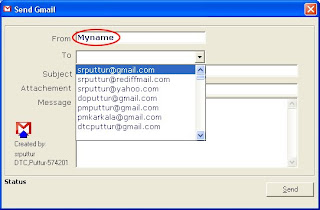 In the next Window,the name of the Sender will appear as per the configuration done in Contacts.ini. You can change here itself if desired. Select the to ID from the Drop down menu. If the ID intended is not added in the contacts.ini file,it will not appear here.You can also type any ID here. Mention the Subject.
In the next Window,the name of the Sender will appear as per the configuration done in Contacts.ini. You can change here itself if desired. Select the to ID from the Drop down menu. If the ID intended is not added in the contacts.ini file,it will not appear here.You can also type any ID here. Mention the Subject.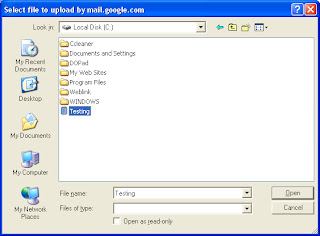 Attachment is not mandatory. If attachment is there, then click Browse button.Select the required file. Any file permissible by Google can be attached.
Attachment is not mandatory. If attachment is there, then click Browse button.Select the required file. Any file permissible by Google can be attached.